Rapid evolution of enterprise IT and the dynamics of growing digital ecosystems introduce organizations to risks associated with third party applications and assets. CISOs and risk managers round the globe fight an endless battle to reduce such threats daily. External Attack Surface Management is a strategic step taken to improve the external asset visibility and reduce the points of entry via an attacker’s perspective of the enterprise infrastructure.
Security teams and vendors may use External Attack Surface Management to:
-
Make a visual sense of how the external infrastructure looks to an adversary
-
Keep track of resources and technologies exposed on the internet
-
Maintain centralized monitoring of infrastructure of owner and child companies
-
Assess and reduce vulnerable assets that allow attackers to get a foothold inside the infrastructure

How Does External Attack Surface Management Work?
External Attack Surface Management does not require an organization to run intensive scans or install agents on their assets and only needs the domains and IP ranges that need to be monitored. This data is then utilized to run searches for associated critical information just like an adversary would do over the internet. This exercise can be scheduled at relative intervals of the customer’s choice where each run may take 1-48 hours. Upon completion, any vulnerabilities in the infrastructure, external malware communications, and critical business information that may be used by adversaries to their advantage is provided in an actionable report.
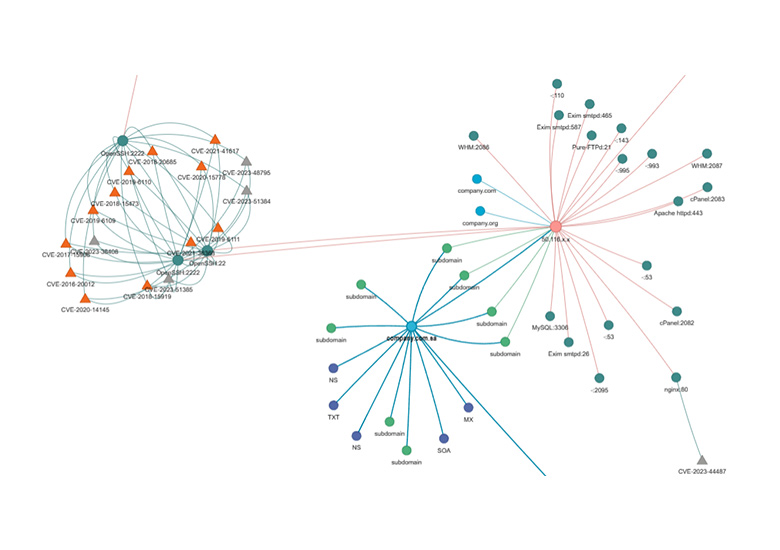
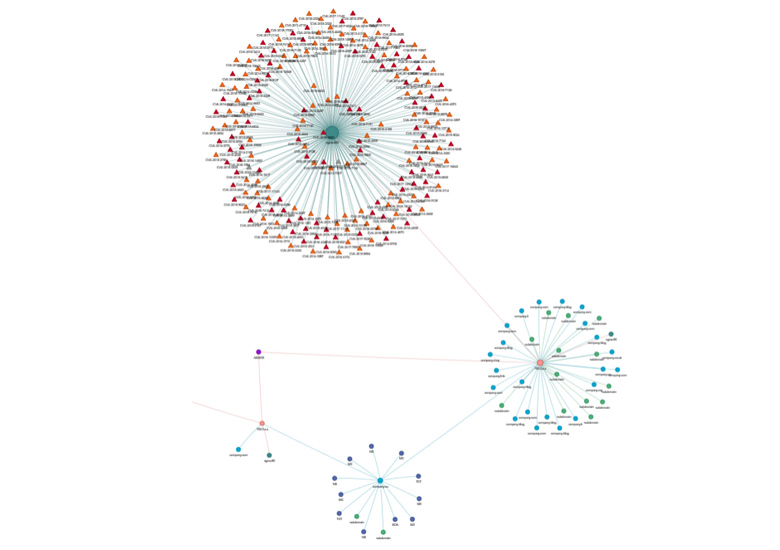
How Does External Attack Surface Management Improve Cyber Resilience?
Assess Vulnerability and Exploit Impact
Know which assets are impacted by a newly released vulnerability and what’s their exploitability.
Real World Scenario
Security team finds that a public move it Transfer server is vulnerable to a CVE that is listed in CISA’s Known Exploited Vulnerabilities Catalog. The security team then prioritizes patching that server and executes a retro-hunt for signs of exploitation.
Identify Unmanaged Assets
Keep track of your assets and monitor your environment daily to find unidentified assets.
Real World Scenario
A security analyst checks the External Attack Surface Management breport and finds an unidentified server running in the environment. The analyst then immediately verifies whether the server was spawned following the change management procedures.
Merger & Acquisition
Be aware of the external security posture and the risks associated with it.
Real World Scenario
A fintech company plans to acquire another firm but wants to perform due diligence before the merger of their user applications. They run an external attack surface assessment and find all the applications, assets and the associated technologies that will integrate with their own application.
